This article is part of the TechXchange: Wireless IoT Technologies.
Members can download this article in PDF format.
What you’ll learn:
- What is LoRaWAN, and how do the technologies that power it work?
- How LoRaWAN's unique modulation scheme and air interface protocol is able to support reliable long-distance communications while consuming extremely low levels of power.
- How using TC/IP as its foundation enables LoRaWAN to work seamlessly with most IoT applications.
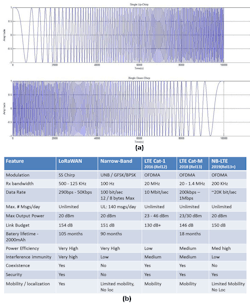
Low-power wireless network (LPWN) technologies such as LoRaWAN (long-range wide area network) and Sigfox help extend the IoT into areas and applications that aren’t practical for 5G services to support. Though their low data rates (250 bits/s to 50 kb/s) and relatively high latency aren’t suitable for some applications, the ability to perform reliably in noisy, congested environments across long distances, while operating for nearly a decade on a single low-voltage battery, make them an excellent solution for many other apps. They include smart agriculture, remote environmental sensing, and monitoring the structural health of bridges, railways, and other critical elements of the national infrastructure (Fig. 1).
Since many of these applications also require low per-node CAPEX/OPEX costs to be feasible, LoRaWAN's open-source specification, use of unlicensed frequency bands, and its ability to leverage existing public networks have helped it gain popularity in many parts of North America, Europe, and elsewhere.
In this article, we'll look at the technologies that underlie the LoRaWAN wireless data standard and a few of the applications it makes possible.
What is LoRaWAN?
LoRaWAN is a type of low-power wide-area network (LPWAN) that uses open-source technology and transmits over unlicensed frequency bands. It’s based on the LoRa protocol,1 which is designed to wirelessly connect battery-operated "things" to the internet in regional, national, or global networks. LoRaWAN was also developed specifically to support the key functional requirements of the Internet of Things (IoT), such as bidirectional communications, end-to-end security, mobility, and localization services.
The protocol operates on the globally available sub-1-GHz ISM bands, enabling low-power embedded radios to use very-low-power transceivers to cover large distances with true bidirectional communications. Instead of the frequency-shift-key (FSK) modulation techniques used by many wireless networks, LoRaWAN employs chirp-spread-spectrum (CSS) modulation2 (Fig. 2a).
CCS modulation maintains the same low-power characteristics as FSK modulation, but it significantly increases the communication range (Fig. 2b). CSS has been proven over decades of use in military and space communication, where its resistance to interference and high coding gain has provided reliable ultra-low communications over long distances.
The Transmission Benefits of LoRa
To further enhance signal integrity, LoRa uses a wide transmission band (typically 125 kHz), which makes it extremely resistant to channel noise, long-term relative frequency, Doppler effects, and fading.
LoRa also adds a unique capability called adaptive data rate (ADR) to increase transmission distance. Geoff Mulligan, creator of the LoRa protocol, explained, "ADR allows the LoRaWAN network to automatically and independently choose the most appropriate output power and data rate for optimal and efficient communications by each device, while controlling the SNR (signal-to-noise ratio) and link budget. Devices that are closer to the base station can transmit at higher data rates, while devices further away transmit at lower rates."
Mulligan added, "This transmission model makes it possible to match the power and speed requirements of a particular application, rather than using a 'one-size-fits-all' approach. By using different ADRs (SF1 through SF12), devices can transmit up to 50 kb/s or over distances up to 20 km with link budgets up to −148 dB. LoRa’s robust link-management scheme enables it to support lower data rates across even larger distances."
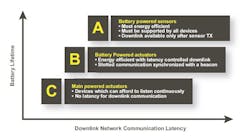
Because different applications have different communication requirements, the LoRaWAN specification supports three different "classes" of devices (Fig. 3):
- Class A (Asynchronous) devices are generally battery-operated sensors that communicate on an as-needed basis. Examples include temperature and motion sensors that send data when triggered by some external anomaly, such as a high or low temperature or sensed motion. In addition, these devices use the "Queen’s Protocol," meaning they can only be spoken to after they have first spoken (i.e., wait for a response after transmitting). Class A devices offer the most power-efficient mode, enabling field deployments of sensor devices that operate for many years on a single battery.
- Class B devices are also generally battery-operated, but with the added capability of enabling the application to send data to the sensor on a predefined time interval (the beacon period). This still provides very-low-power operations, while allowing for efficient two-way communications that don’t require the application to wait for communication from the sensor or end device. Using a Class B device can reduce the battery lifetime, but at the same time, it significantly reduces latency and provides deterministic communication.
- Class C devices are "mains-powered" in most cases, or have some sort of external power source (e.g., photovoltaic). These end points are "always on" and listening for messages from the application. A typical use for a Class C device is to provide communications for an actuator or controller. Here, the application can send commands or data to the end point whenever necessary, thereby nearly eliminating the latencies of other device classes, but with higher power consumption.
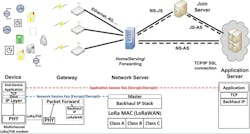
To make the most effective use of its wireless protocol, the LoRa Alliance chose a star-type network topology. It’s similar to the topology used by Wi-Fi networks (with endpoints and access points), with one significant difference: All access points receive messages transmitted by end points (Fig. 4).
That very important difference gives LoRaWAN some unique capabilities. First and foremost, the LoRaWAN protocol makes use of the fact that radio transmissions are "broadcast," meaning many devices can and will receive the transmitted message.
Unlike the unicast messaging protocol used by ZigBee, Bluetooth, and Wi-Fi, the LoRaWAN protocol provides a more robust communication path and eliminates the single points of failure that are common in these other systems. And, by designing in the concept of multiple independent receivers, the LoRaWAN protocol can provide intrinsic support for endpoint geolocation without resorting to power- hungry and expensive GPS radios. Instead, LoRaWAN nodes can apply a technique called time difference of arrival (TDOA) to triangulate the precise location of any endpoint.
LoRaWAN Built with Bottom-Up Security
Security was a primary consideration during the development of the LoRaWAN protocol. As a result, security and intrusion resistance is baked into its DNA.
The protocol's architecture utilizes two separate AES keys (Advanced Encryption Standard, developed by NIST and adopted by the U.S. government). The first key (the network session key, as seen in Figure 4) is used to protect and secure data during transmission across the LoRaWAN network. The second key (the application session key) is used to protect and secure the data end-to-end from the endpoint to the sensor application.
The purpose for using two distinct keys is to permit devices to roam from one network to another. The network session key is known only to the endpoints and the local network, while the application session key is only known to the endpoint and end-sensor application.
In this way, a device can move from one network to another (roam), and the network can ensure that packets not be intercepted or inserted into the local network (that the network is secure). At the same time, the end device and application can be assured of the data’s confidentiality and integrity, no matter which network is used to transfer the data.
Part 2 of this series looks at how LoRaWAN can be used to bring the intelligence of the IoT to agriculture, commerce, and a wide range of other public infrastructure applications.
Read more articles in the TechXchange: Wireless IoT Technologies.
References
1. "LoRa and LoRaWAN: A Technical Overview," Semtech, 2019.
2. Umber Noreen, Ahc`ene Bounceur, Laurent Clavier, "A Study of LoRa Low Power and Wide Area Network Technology," ATSIP'2017.
3. "What Is LoRa?," LoRa Alliance.
4. LoRaWAN Technical Specifications, LoRa Alliance.
Additional white papers on wireless security, LPWA technology, applications, and other topics may be found on the LoRa Alliance website.